
Accelerating Deployments with AWS ECS
May 1, 2025
Five Cloud Mistakes
August 1, 2025Executive Summary
This GitLab Runner Case Study explores how KineticSkunk revamped its CI/CD systems by deploying a bespoke fleet of custom GitLab Runners. The result? More than 70% faster validation, real-time feedback, hardened security, and a self-healing build pipeline. This GitLab Runner Case Study outlines how custom runners transformed performance metrics, making it a blueprint for future CI/CD implementations.
Background and Objectives – GitLab Runner Case Study
As a consultancy operating across AWS, Azure, and Red Hat OpenShift, KineticSkunk needed to evolve beyond legacy Jenkins and static agents. The main goals included:
- Accelerate feedback loops on feature branches
- Secure builds using vault-managed credentials
- Scale automatically to handle test surges
- Standardize job templates across services
These objectives required a scalable, high-availability solution without compromising compliance or development velocity.
Key Challenges – GitLab Runner Case Study
The team faced several friction points that made rapid delivery difficult:
- Agent Pool Saturation: Shared runners couldn’t handle spikes from heavy test jobs, especially Selenium and GenAI suites.
- Configuration Drift: Tooling inconsistencies led to brittle pipelines.
- Secrets Management: Needed secure, one-time secret injection during builds.
- Availability Risks: Single-AZ agents posed operational exposure.
GitLab Auto-scaling Runner Solution Architecture
To tackle these problems, KineticSkunk adopted a robust architecture optimized for automation, consistency, and fault tolerance.
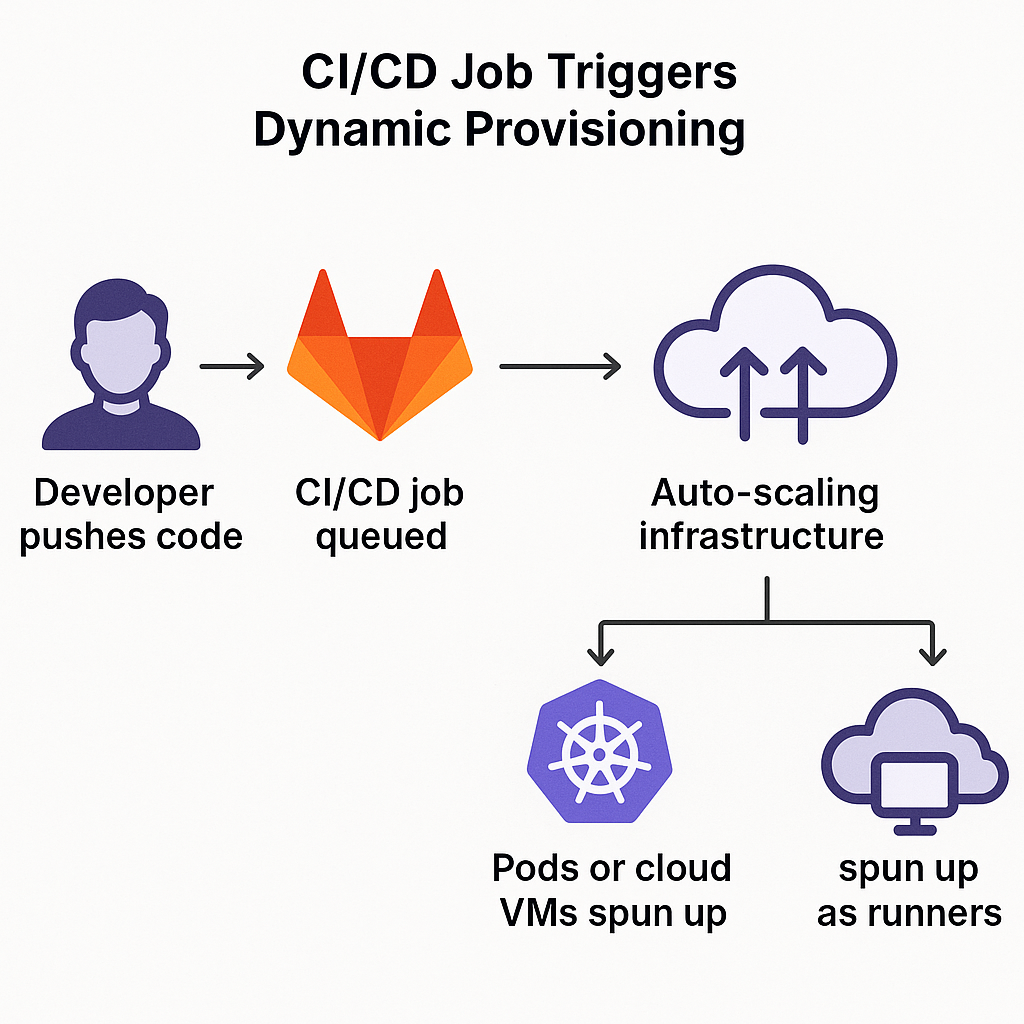
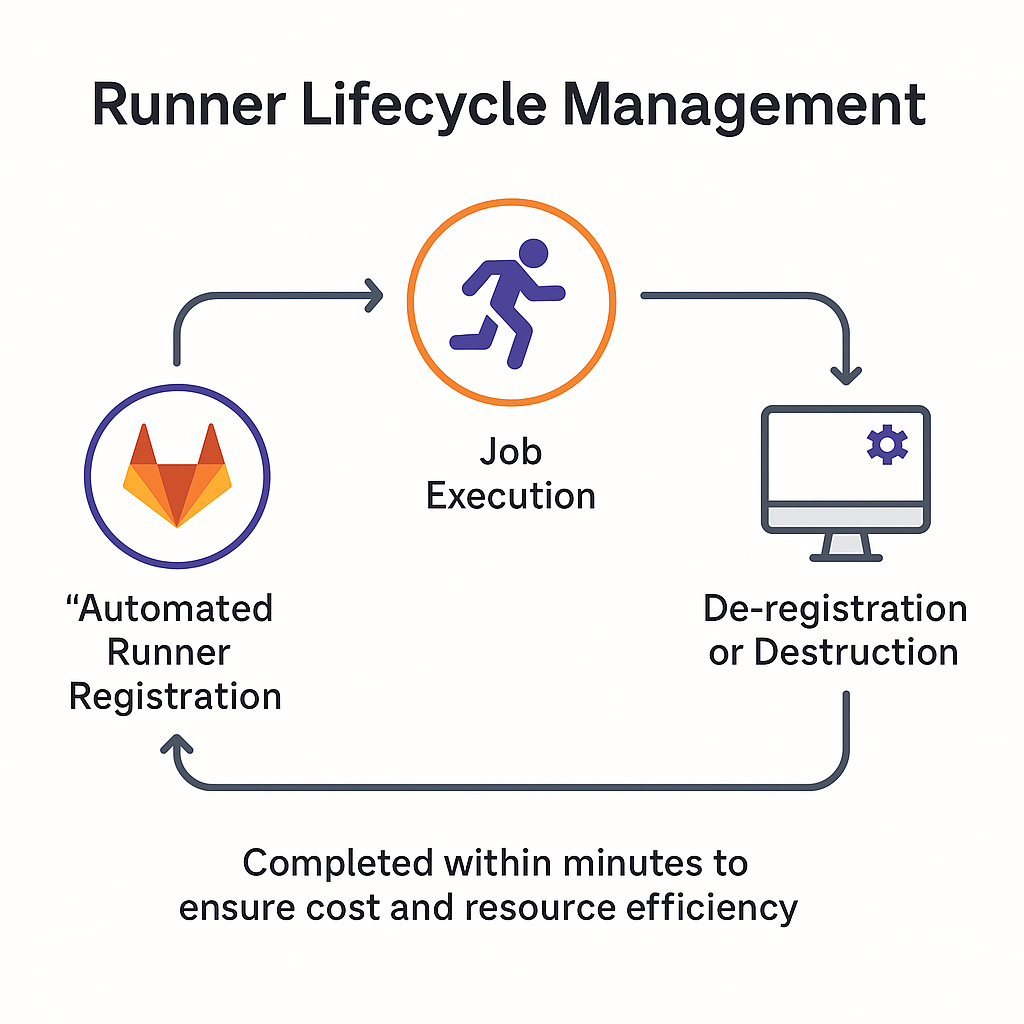
Gitlab Dynamic Agent Provisioning
Auto-scaling runners were deployed using Kubernetes and cloud VMs, triggered per-job and decommissioned afterward to ensure elasticity.
Gitlab Immutable Configuration Templates
All job definitions were consolidated into centrally managed YAML templates, preventing drift and promoting reusability.
Gitlab Secure Secret Injection
Integrated with HashiCorp Vault, pipelines retrieved time-limited tokens without storing sensitive data locally.
Learn more about HashiCorp Vault’s secrets engine and how it integrates with CI/CD systems.

Gitlab Multi-Zone Resilience
Runners spanned multiple availability zones, equipped with health checks and auto-recovery via a monitoring system to prevent outages.


Implementation Components
| Component | Approach |
|---|---|
| Agent Pools | EKS pods and cloud VMs with cleanup hooks |
| Job Dispatch Logic | Pipeline tagging and workload prioritization |
| Configuration Store | Git-backed YAML templates and approval workflows |
| Observability | Real-time metrics, queue monitoring, and auto-scaling triggers |
Results & Metrics
- Queue Reduction: 75% less wait time during traffic surges
- Runtime Efficiency: 60% faster execution across most jobs
- High Availability: >99.9% uptime, with no CI-induced outages
- Security Compliance: No persistent secrets, full audit trail verified
CI/CD Infrastructure Case Study Lessons Learned
- Template Governance: Enforcing shared YAML patterns removed 90% of configuration-related errors
- Autoscaling Lag: Reduced startup delay with leaner runner images
- Infrastructure Redundancy: Moving to multi-zone saved hours of downtime during an unplanned event
Conclusion
This GitLab Runner Case Study highlights how KineticSkunk successfully modernised its CI/CD infrastructure through custom, auto-scaling runners. By addressing core challenges like performance bottlenecks, secrets management, and infrastructure resilience, the team achieved measurable gains—cutting job runtimes by 60% and ensuring over 99.9% availability. The approach combined dynamic provisioning, Vault-based credential injection, and centralised configuration governance, setting a new standard for scalable, secure DevOps pipelines. As organisations continue to demand faster, safer software delivery, this case study proves the value of investing in tailored GitLab Runner solutions.
Explore Our DevOps & DevSecOps Solutions
Looking to optimize your CI/CD pipelines or enhance cloud security? Discover how our tailored solutions can drive efficiency, resilience, and compliance:
DevOps Solutions
- CI/CD pipeline design and automation
- Infrastructure as Code (IaC) using Terraform, Pulumi, or Ansible
- Cloud-native deployments on AWS, Azure, GCP
- Kubernetes orchestration and scaling
- Monitoring, logging, and observability systems
DevSecOps Solutions
- Secure pipeline design with integrated security checks
- Secrets management with Vault, AWS Secrets Manager, etc.
- Static and dynamic security testing (SAST/DAST)
- Compliance automation and audit readiness
- Container image scanning and policy enforcement
Learn more:
DevOps Solutions | DevSecOps Solutions




